Binary Exploitation
(Thank you @numonce)
Overview¶
Binary exploitation is the process of subverting a compiled application such that it violates some trust boundary in a way that is advantageous to you, the attacker. We'll be focusing on memory corruption types in this section, since that's what's covered in OSCP. Unlike the PWK/OSCP course we'll be using radare2, because I like it. We won't be covering the basics of assembly, so if you want something that can give you a pretty good idea in under 2 hours check Liveoverflow's Binary Exploitation playlist on YouTube.
White box¶
White box simply means we have the source code of the program that we're given the executable that we're trying to exploit. Let's take a simple gets() exploit program.
Info
If you're following along, compile with gcc -m32 test.c -o test -fno-stack-protector -no-pie and disable aslr
#include <stdio.h>
#include <stdlib.h>
int main() {
char a[65];
printf("This is totally safe code.\n");
gets(a);
}
gets() is a inherently unsafe function because it has no built in mechanism to check the size of user input. Meaning, that we can send input of an arbitrary size to the a array that can only hold 65 bytes. now we could take over the IP (Instruction pointer) registry after sending more that 65 bytes (including the null byte at the end).
This doesn't crash because we filled the buffer without overflowing it.
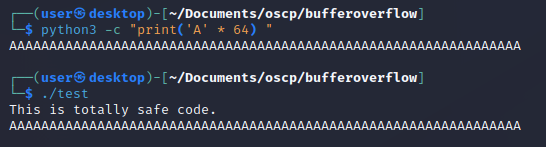
This didn't overflow because we filled the buffer all the way up to the correct limit, but adding just a single byte will make it segfault.
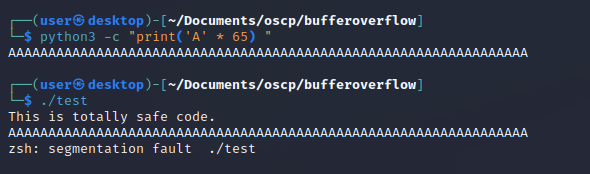
The total amount of bytes it takes to get to the IP is completely dependent on the compiler, so it's good practice to use a debugger like radare2 for this.
Warning
Binary exploitation is a really vast topic, and being that OSCP no longer guarantees the use of a bufferflow, and even if it does, is guaranteed not to be apart of AD I won't be continuing notes on this subject.